AWS PrivateLink Connectivity
AWS PrivateLink allows you to open a path to Temporal without opening a public egress. It establishes a private connection between your Amazon Virtual Private Cloud (VPC) and Temporal Cloud. This one-way connection means Temporal cannot establish a connection back to your service. This is useful if normally you block traffic egress as part of your security protocols. If you use a private environment that does not allow external connectivity, you will remain isolated.
Creating an AWS PrivateLink connection
Set up PrivateLink connectivity with Temporal Cloud with these steps:
-
Open the AWS console with the region you want to use to establish the PrivateLink.
-
Search for "VPC" in Services and select the option.
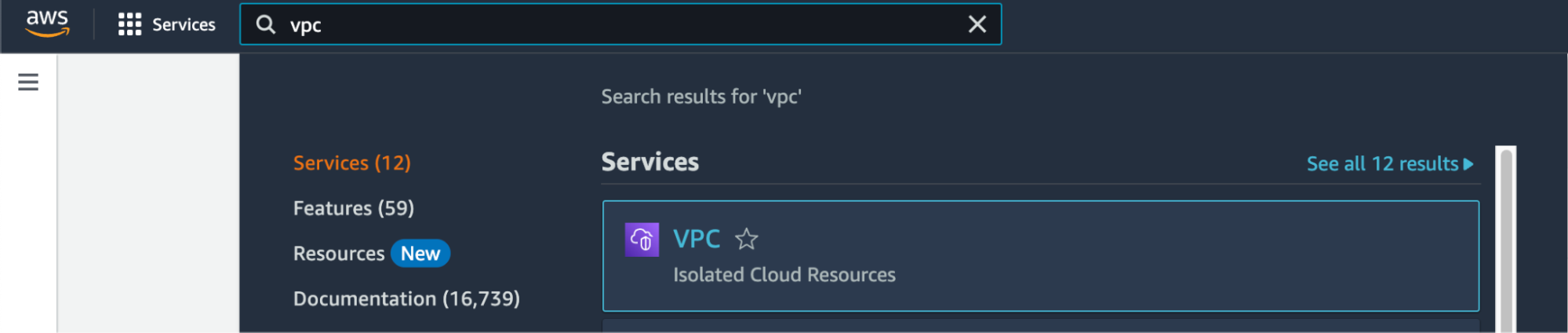
-
Select Virtual private cloud > Endpoints from the left menu bar.
-
Click the Create endpoint button to the right of the Actions pulldown menu.
-
Under Type category, select Endpoint services that use NLBs and GWLBs. This option lets you find services shared with you by service name.
-
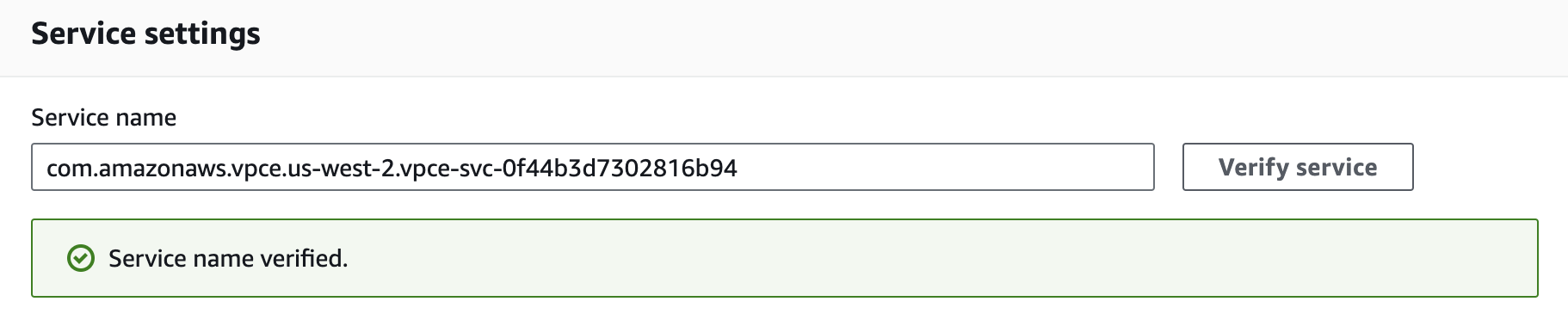
Under Service settings, fill in the Service name with the PrivateLink Service Name for the region you’re trying to connect from:
Region PrivateLink Service Name ap-northeast-1com.amazonaws.vpce.ap-northeast-1.vpce-svc-08f34c33f9fb8a48aap-northeast-2com.amazonaws.vpce.ap-northeast-2.vpce-svc-08c4d5445a5aad308ap-south-1com.amazonaws.vpce.ap-south-1.vpce-svc-0ad4f8ed56db15662ap-south-2com.amazonaws.vpce.ap-south-2.vpce-svc-08bcf602b646c69c1ap-southeast-1com.amazonaws.vpce.ap-southeast-1.vpce-svc-05c24096fa89b0ccdap-southeast-2com.amazonaws.vpce.ap-southeast-2.vpce-svc-0634f9628e3c15b08ca-central-1com.amazonaws.vpce.ca-central-1.vpce-svc-080a781925d0b1d9deu-central-1com.amazonaws.vpce.eu-central-1.vpce-svc-073a419b36663a0f3eu-west-1com.amazonaws.vpce.eu-west-1.vpce-svc-04388e89f3479b739eu-west-2com.amazonaws.vpce.eu-west-2.vpce-svc-0ac7f9f07e7fb5695sa-east-1com.amazonaws.vpce.sa-east-1.vpce-svc-0ca67a102f3ce525aus-east-1com.amazonaws.vpce.us-east-1.vpce-svc-0822256b6575ea37fus-east-2com.amazonaws.vpce.us-east-2.vpce-svc-01b8dccfc6660d9d4us-west-2com.amazonaws.vpce.us-west-2.vpce-svc-0f44b3d7302816b94 -
Confirm your service by clicking on the Verify service button. AWS should respond "Service name verified."
-
Select the VPC and subnets to peer with the Temporal Cloud service endpoint.
-
Select the security group that will control traffic sources for this VPC endpoint. The security group must accept TCP ingress traffic to port 7233 for gRPC communication with Temporal Cloud.
-
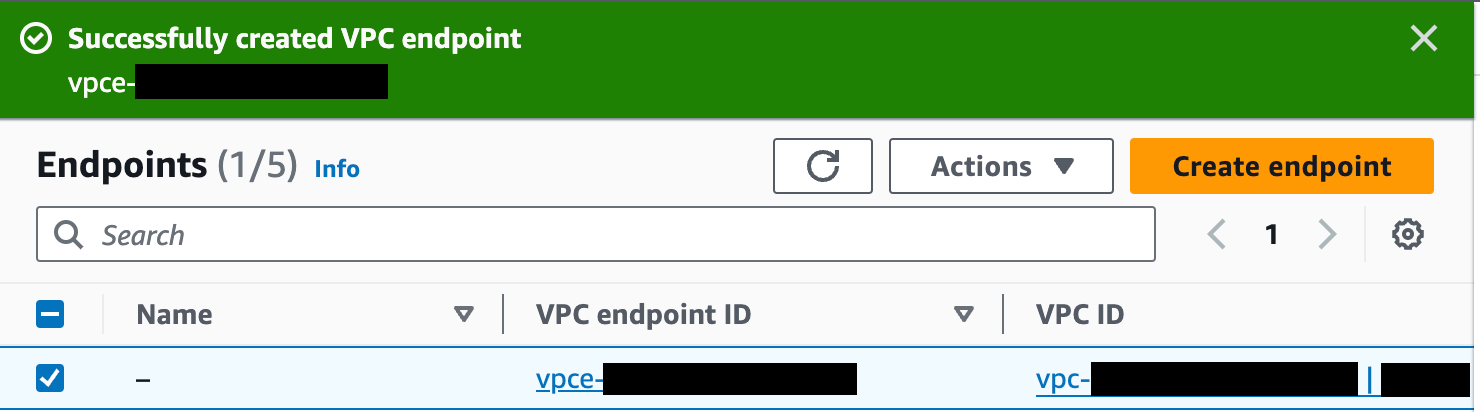
Click the Create endpoint button at the bottom of the screen. If successful, AWS reports "Successfully created VPC endpoint." and lists the new endpoint. The new endpoint appears in the Endpoints list, along with its ID.
-
Click on the VPC endpoint ID in the Endpoints list to check its status. Wait for the status to be “Available”. This can take up to 10 minutes.
-
Once available, you can use AWS PrivateLink. Use the first value under “DNS names” as your hostname to connect to Temporal Cloud using port 7233. To establish a valid mTLS session, you must override the TLS server name used for the connection to
<namespace_id>.<account_id>.tmprl.cloud. Alternatively, you can configure private DNS for AWS PrivateLink.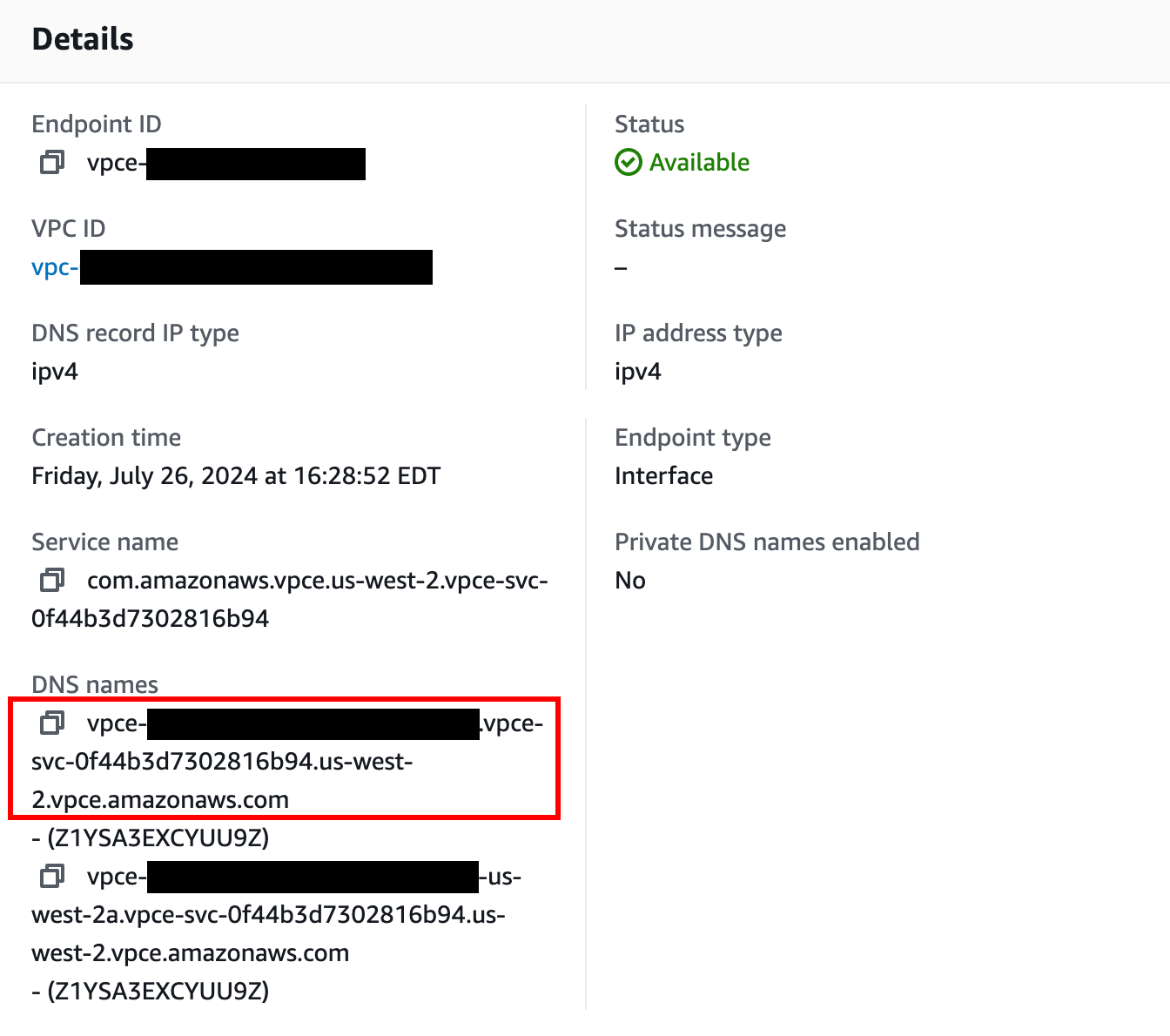
You are ready to start using Private Link with Temporal Cloud.
PrivateLink endpoint services are regional. Individual Namespaces do not use separate services.
Once set up, you can test your PrivateLink connectivity using the following methods.
When connecting, you must override the TLS server name to target your Namespace’s individual hostname (<namespace_id>.<account_id>.tmprl.cloud) to establish a valid mTLS session:
-
The Temporal CLI, using the
--tls-server-nameparameter to override the TLS server name. For example:temporal workflow count \
--address <DNS associated with VPC endpoint>:7233 \
--tls-cert-path /path/to/client.pem \
--tls-key-path /path/to/client.key \
--tls-server-name <namespace_id>.<account_id>.tmprl.cloud \
--namespace <namespace_id>.<account_id> -
Non-Temporal tools like grpcURL, useful for testing from environments that restrict tool usage, using the
-servernameparameter to override the TLS server name. For example:grpcurl \
-servername <namespace_id>.<account_id>.tmprl.cloud \
-cert /path/to/client.pem \
-key /path/to/client.key \
<DNS ASSOCIATED WITH VPC ENDPOINT>:7233 \
temporal.api.workflowservice.v1.WorkflowService/GetSystemInfo -
Temporal SDKs, by setting the endpoint server address argument to the PrivateLink endpoint (
<DNS associated with VPC endpoint>:7233) and using the TLS configuration options to override the TLS server name.
When using API keys for namespace authentication, the TLS server name must be set to the Namespace's gRPC endpoint (<region>.<cloud_provider>.api.temporal.io) using one of the following methods:
-
The Temporal CLI, using
--tls-server-nameparameter to override the TLS server name and the--tlsflag to enforce the use of TLS. For example:temporal workflow count \
--address <DNS associated with VPC endpoint>:7233 \
--namespace <namespace>.<account> \
--api-key <api_key> \
--tls-server-name <region>.<cloud_provider>.api.temporal.io \
--tls -
Non-Temporal tools like grpcURL, setting the
authorizationandtemporal-namespaceheaders, and the-servernameparameter to override the TLS server name. For example:grpcurl \
-H "authorization: Bearer <api_key>" \
-H "temporal-namespace: <namespace>.<account>" \
-servername <region>.<cloud_provider>.api.temporal.io \
<DNS ASSOCIATED WITH VPC ENDPOINT>:7233 \
temporal.api.workflowservice.v1.WorkflowService/GetSystemInfo
Configuring Private DNS for AWS PrivateLink
Why configure private DNS?
When you connect to Temporal Cloud through AWS PrivateLink you normally must:
- Point your SDKs/Workers at the PrivateLink DNS name for the VPC Endpoint (e.g.,
vpce-0123456789abcdef-abc.us-east-1.vpce.amazonaws.com), and - Override the Server Name Indicator (SNI) so that the TLS handshake still presents the public Temporal Cloud hostname (e.g.,
my-namespace.my-account.tmprl.cloud).
By creating a Route 53 private hosted zone (PHZ) that maps the public Temporal Cloud hostname (or region hostname) to your VPC Endpoint, you can:
- Keep using the standard Temporal Cloud hostnames in code and configuration.
- Eliminate the need to set a custom SNI override.
- Make future Endpoint rotations transparent—only the PHZ record changes.
This approach is optional; Temporal Cloud works without it. It simply streamlines configuration and operations.
Prerequisites
| Requirement | Notes |
|---|---|
| AWS VPC with DNS resolution and DNS hostnames enabled | VPC console → Edit DNS settings → enable both checkboxes. |
| Interface VPC Endpoint for Temporal Cloud | Subnets must be associated with the VPC and Security Group must allow TCP ingress traffic to port 7233 from the appropriate hosts. |
| Route 53 available in your AWS account | You need permission to create Private Hosted Zones and records. |
| Namespace details | Needed to choose the correct override domain pattern below. |
Choose the override domain and endpoint
| Temporal Cloud setup | Use this PHZ domain | Example |
|---|---|---|
| Single-region namespace with mTLS auth | <account>.tmprl.cloud | payments.abcde.tmprl.cloud ↔ vpce-... |
| Multi-region namespace or API-key auth | region.tmprl.cloud | aws-us-east-1.region.tmprl.cloud ↔ vpce-... |
Step-by-step instructions
1. Collect your PrivateLink endpoint DNS name
aws ec2 describe-vpc-endpoints \
--vpc-endpoint-ids $VPC_ENDPOINT_ID \
--query "VpcEndpoints[0].DnsEntries[0].DnsName" \
--output text
# Example output:
# vpce-0123456789abcdef-abc.us-east-1.vpce.amazonaws.com
Save the vpce-*.amazonaws.com value -- you will target it in the CNAME record.
2. Create a Route 53 Private Hosted Zone
- Open Route 53 → Hosted zones → Create hosted zone.
- Enter the domain chosen from the table above, e.g.,
payments.abcde.tmprl.cloud. - Type: Private hosted zone for Temporal Cloud.
- Associate the hosted zone with every VPC that contains Temporal Workers and/or SDK clients.
- Create hosted zone.
3. Add a CNAME record
Inside the new PHZ:
| Field | Value |
|---|---|
| Record name | the namespace endpoint (e.g., payments.abcde.tmprl.cloud). |
| Record type | CNAME |
| Value | Your VPC Endpoint DNS name (vpce-0123456789abcdef-abc.us-east-1.vpce.amazonaws.com) |
| TTL | 60s is typical; 15s for MRN namespaces; adjust as needed. |
4. Verify DNS resolution from inside the VPC
dig payments.abcde.tmprl.cloud
If the record resolves to the VPC Endpoint, you are ready to use Temporal Cloud without SNI overrides.
Updating your workers/clients
With private DNS in place, configure your SDKs exactly as the public-internet examples show (filling in your own namespace):
clientOptions := client.Options{
HostPort: "payments.abcde.tmprl.cloud:7233",
Namespace: "payments",
// No TLS SNI override needed
}
The DNS resolver inside your VPC returns the private endpoint, while TLS still validates the original hostname—simplifying both code and certificate management.
Configure Private DNS for Multi-Region Namespaces
Proper networking configuration is required for failover to be transparent to clients and workers when using PrivateLink. This page describes how to configure routing for Namespaces with High Availability features on AWS PrivateLink.
To use AWS PrivateLink with High Availability features, you may need to:
- Override the regional DNS zone.
- Ensure network connectivity between the two regions.
This page provides the details you need to set this up.
Customer side solutions
When using PrivateLink, you connect to Temporal Cloud through a VPC Endpoint, which uses addresses local to your network.
Temporal treats each region.<tmprl_domain> as a separate zone.
This setup allows you to override the default zone, ensuring that traffic is routed internally for the regions you’re using.
A Namespace's active region is reflected in the target of a CNAME record. For example, if the active region of a Namespace is AWS us-west-2, the DNS configuration would look like this:
| Record name | Record type | Value |
|---|---|---|
| ha-namespace.account-id.tmprl.cloud | CNAME | aws-us-west-2.region.tmprl.cloud |
After a failover, the CNAME record will be updated to point to the failover region, for example:
| Record name | Record type | Value |
|---|---|---|
| ha-namespace.account-id.tmprl.cloud | CNAME | aws-us-east-1.region.tmprl.cloud |
The Temporal domain did not change, but the CNAME updated from us-west-2 to us-east-1.
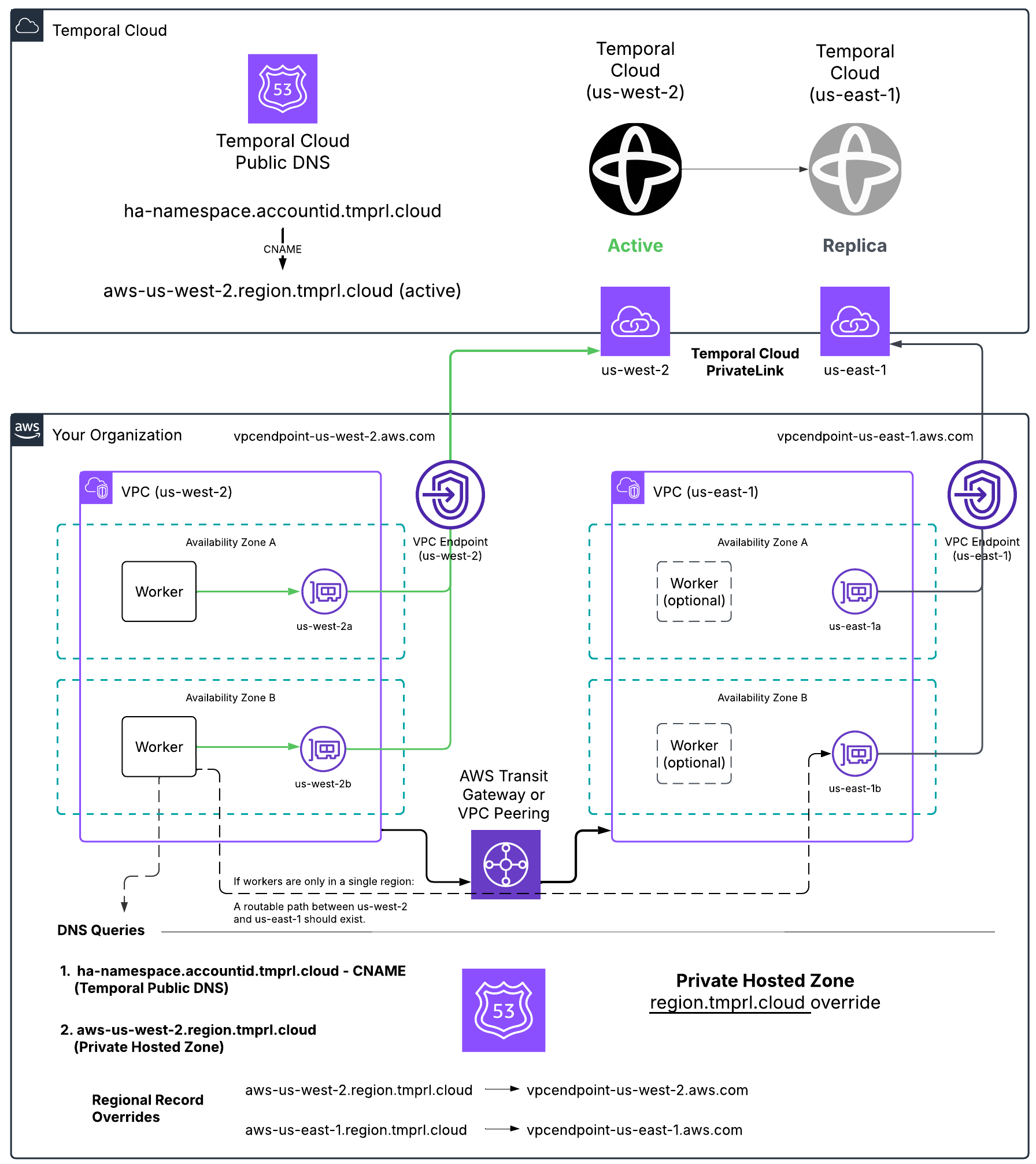
Customer side solution example
Setting up the DNS override
To set up the DNS override, configure specific regions to target the internal VPC Endpoint IP addresses.
For example, you might set aws-us-west-1.region.tmprl.cloud to target 192.168.1.2.
In AWS, this can be done using a Route 53 private hosted zone for region.tmprl.cloud.
Link that private zone to the VPCs you use for Workers.
When your Workers connect to the Namespace, they first resolve the <ns>.<acct>.<tmprl_domain> record.
This points to <aws-active-region>.region.tmprl.cloud, which then resolves to your internal IP addresses.
Consider how you’ll configure Workers for this setup. You can either have Workers run in both regions continuously or establish connectivity between regions using Transit Gateway or VPC Peering. This way, Workers can access the newly activated region once failover occurs.
Available regions, PrivateLink endpoints, and DNS record overrides
The following table lists the available Temporal regions, PrivateLink endpoints, and regional endpoints used for DNS record overrides:
Asia Pacific - Tokyo (ap-northeast-1)
- Cloud API Code:
aws-ap-northeast-1 - Regional Endpoint:
aws-ap-northeast-1.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.ap-northeast-1.vpce-svc-08f34c33f9fb8a48a - Same Region Replication: Not Available
- Multi-Region Replication:
aws-ap-northeast-2aws-ap-south-1aws-ap-south-2aws-ap-southeast-1aws-ap-southeast-2
- Multi-Cloud Replication:
gcp-asia-south1
Asia Pacific - Seoul (ap-northeast-2)
- Cloud API Code:
aws-ap-northeast-2 - Regional Endpoint:
aws-ap-northeast-2.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.ap-northeast-2.vpce-svc-08c4d5445a5aad308 - Same Region Replication: Not Available
- Multi-Region Replication:
aws-ap-northeast-1aws-ap-south-1aws-ap-south-2aws-ap-southeast-1aws-ap-southeast-2
- Multi-Cloud Replication:
gcp-asia-south1
Asia Pacific - Mumbai (ap-south-1)
- Cloud API Code:
aws-ap-south-1 - Regional Endpoint:
aws-ap-south-1.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.ap-south-1.vpce-svc-0ad4f8ed56db15662 - Same Region Replication: Not Available
- Multi-Region Replication:
aws-ap-northeast-1aws-ap-northeast-2aws-ap-south-2aws-ap-southeast-1aws-ap-southeast-2
- Multi-Cloud Replication:
gcp-asia-south1
Asia Pacific - Hyderabad (ap-south-2)
- Cloud API Code:
aws-ap-south-2 - Regional Endpoint:
aws-ap-south-2.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.ap-south-2.vpce-svc-08bcf602b646c69c1 - Same Region Replication: Not Available
- Multi-Region Replication:
aws-ap-northeast-1aws-ap-northeast-2aws-ap-south-1aws-ap-southeast-1aws-ap-southeast-2
- Multi-Cloud Replication:
gcp-asia-south1
Asia Pacific - Singapore (ap-southeast-1)
- Cloud API Code:
aws-ap-southeast-1 - Regional Endpoint:
aws-ap-southeast-1.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.ap-southeast-1.vpce-svc-05c24096fa89b0ccd - Same Region Replication: Not Available
- Multi-Region Replication:
aws-ap-northeast-1aws-ap-northeast-2aws-ap-south-1aws-ap-south-2aws-ap-southeast-2
- Multi-Cloud Replication:
gcp-asia-south1
Asia Pacific - Sydney (ap-southeast-2)
- Cloud API Code:
aws-ap-southeast-2 - Regional Endpoint:
aws-ap-southeast-2.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.ap-southeast-2.vpce-svc-0634f9628e3c15b08 - Same Region Replication: Not Available
- Multi-Region Replication:
aws-ap-northeast-1aws-ap-northeast-2aws-ap-south-1aws-ap-south-2aws-ap-southeast-1
- Multi-Cloud Replication:
gcp-asia-south1
Europe - Frankfurt (eu-central-1)
- Cloud API Code:
aws-eu-central-1 - Regional Endpoint:
aws-eu-central-1.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.eu-central-1.vpce-svc-073a419b36663a0f3 - Same Region Replication: Not Available
- Multi-Region Replication:
aws-eu-west-1aws-eu-west-2
- Multi-Cloud Replication:
gcp-europe-west3
Europe - Ireland (eu-west-1)
- Cloud API Code:
aws-eu-west-1 - Regional Endpoint:
aws-eu-west-1.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.eu-west-1.vpce-svc-04388e89f3479b739 - Same Region Replication: Not Available
- Multi-Region Replication:
aws-eu-central-1aws-eu-west-2
- Multi-Cloud Replication:
gcp-europe-west3
Europe - London (eu-west-2)
- Cloud API Code:
aws-eu-west-2 - Regional Endpoint:
aws-eu-west-2.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.eu-west-2.vpce-svc-0ac7f9f07e7fb5695 - Same Region Replication: Not Available
- Multi-Region Replication:
aws-eu-central-1aws-eu-west-1
- Multi-Cloud Replication:
gcp-europe-west3
North America - Central Canada (ca-central-1)
- Cloud API Code:
aws-ca-central-1 - PrivateLink Endpoint Service:
com.amazonaws.vpce.ca-central-1.vpce-svc-080a781925d0b1d9d - Regional Endpoint:
aws-ca-central-1.region.tmprl.cloud - Same Region Replication: Not Available
- Multi-Region Replication:
aws-us-east-1aws-us-east-2aws-us-west-2
- Multi-Cloud Replication:
gcp-us-central1gcp-us-west1gcp-us-east4
North America - Northern Virginia (us-east-1)
- Cloud API Code:
aws-us-east-1 - Regional Endpoint:
aws-us-east-1.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.us-east-1.vpce-svc-0822256b6575ea37f - Same Region Replication: Available
- Multi-Region Replication:
aws-ca-central-1aws-us-east-2aws-us-west-2
- Multi-Cloud Replication:
gcp-us-central1gcp-us-west1gcp-us-east4
North America - Ohio (us-east-2)
- Cloud API Code:
aws-us-east-2 - Regional Endpoint:
aws-us-east-2.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.us-east-2.vpce-svc-01b8dccfc6660d9d4 - Same Region Replication: Not Available
- Multi-Region Replication:
aws-ca-central-1aws-us-east-1aws-us-west-2
- Multi-Cloud Replication:
gcp-us-central1gcp-us-west1gcp-us-east4
North America - Oregon (us-west-2)
- Cloud API Code:
aws-us-west-2 - Regional Endpoint:
aws-us-west-2.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.us-west-2.vpce-svc-0f44b3d7302816b94 - Same Region Replication: Available
- Multi-Region Replication:
aws-ca-central-1aws-us-east-1aws-us-east-2
- Multi-Cloud Replication:
gcp-us-central1gcp-us-west1gcp-us-east4
South America - São Paulo (sa-east-1)
- Cloud API Code:
aws-sa-east-1 - Regional Endpoint:
aws-sa-east-1.region.tmprl.cloud - PrivateLink Endpoint Service:
com.amazonaws.vpce.sa-east-1.vpce-svc-0ca67a102f3ce525a - Same Region Replication: Not Available
- Multi-Region Replication:
- None
- Multi-Cloud Replication:
- None